Azure Active Directory Privileged Identity Management
How can Microsoft Azure Privileged Identity Management (PIM) help to keep your businesses data and applications secure?

What is Azure AD Privileged Identity Management?
Privileged Identity Management, or PIM, is a found in Azure Active Directory to allow you to manage, control, and monitor access to important services and resources in your business. This includes resources in Azure, Azure Active Directory, Microsoft 365, Microsoft Intune and many others.
Reasons to use Azure AD Privileged Identity Management
Businesses may want to reduce the number of users who have access to secure information, services or resources. This will also minimise the chance of;
• A malicious individual gaining access to this data.
• An authorised user unintentionally impacting sensitive resources or services.
However in many businesses, many of these users still need to carry out elevated permission actions and operations in many of your business services such as; Azure, Azure Active Directory, Azure SQL, Microsoft 365 and other SaaS applications. Businesses are able to grant their users ‘just-in-time’ Privileged Access to Azure and Azure AD services and resources, this will also give businesses the ability to monitor the actions those users are doing when they have Privileged Access.
Licence Requirements
Microsoft Azure Active Directory Privileged Identity Management requires the Azure AD Premium P2 License.
Speak to us about how Microsoft Azure can help your business transition to Cloud Computing.
What does Azure Privileged Identity Management do?
Privileged Identity Management allows you to grant Time-Based and Approval-Based Privilaged Elevation to minimise the risks of unrequired or misused Elevated Access on services or resources that are key to your business. Some of the primary features of Privileged Identity Management or:
• Supply ‘just-in-time’ Privileged Access to Azure, Azure Active Directory and other Azure services and resources.
• Alocate time based elevated access to services and resources with start and end times.
• Require approval to activate privileged access roles.
• Require multi-factor authentication, or MFA, to activate any role elevation.
• Receive notifications when Privileged Access roles are provided to users.
• Review access role to ensure users still require Privileged Access.
• View an Audit History for Internal or External Review.
• Stops the removal of the last Global Administrator user role assignment.
What can you do with Azure Privileged Identity Management?
When you set up Azure Privileged Identity Management, in your left navigation menu, you will options for; Tasks, Manage, and Activity. As an Administrator, you will be able to choose between options such as being able to manage Azure Aactive Directory user roles, manage Azure service or resource roles, as well as Privileged Access groups. Once you have chosen what you want to manage, you will then be able to see the relevant actions for that option.
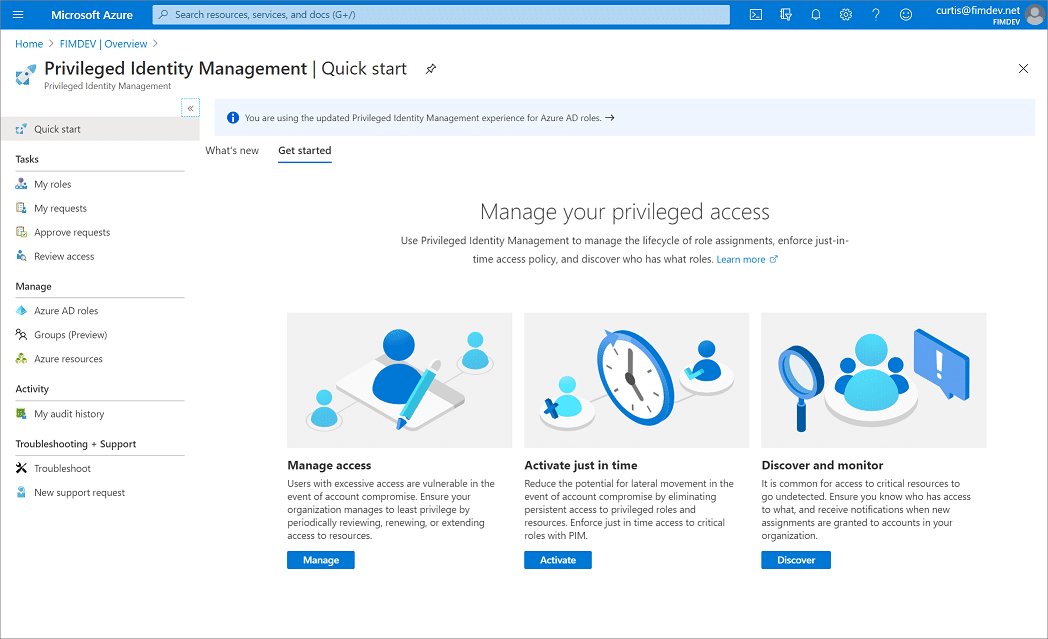
Who is able to do what?
Only a users who are in the Privileged User Role ‘Administrator’ or ‘Global Administrator’ are able to manage user role assignments for other administrators.
Users who are ‘Global Administrators’, ‘Security Administrators’, ‘Global Readers’, and ‘Security Readers’ are able view assignments of Azure Active Directory user roles in Privileged Identity Management.
As for Microsoft Azure resource user roles in Privileged Identity Management, only a user who has the role of ‘Subscription Administrator’, a resource ‘Owner’, or a resource ‘User Access Administrator’ are able to manage assignments of administrators. Members who are ‘Privileged Role Administrators’, ‘Security Administrators’, or ‘Security Readers’, by default, do not have access to view the assignments to Azure resource roles within Privileged Identity Management.
Terminology
To understand Privileged Identity Management and the documentation surrounding it, it is best to review the following terminology;
| Term/Concept | Role Assignment Category | Description |
| Active | Type | This does not require the user to perform any actions to use this role and users with these roles have the privileges assigned to that role. |
| Permanent Active | Duration | Users will always have access to these roles without the requirement to perform any further actions. |
| Time Bound Active | Duration | Users will only have access to these roles within specified start and end times. |
| Activate | This is the process of performing actions to use a role that users are eligible for. This may include actions such as Multi-Factor Authentication (MFA) checks, providing justifications for using the role or requiring further approval from designated approvers within the business. | |
| Activated | State | A user has performed the required prerequisites to ‘Activate’ their role and it is now ‘Active’. |
| Assigned | State | The user has an active role assignment. |
| Eligible | Type | If a user is eligible for a role, it means that they will be able to ‘Activate’ the role by performing the required prerequisites. |
| Permanent Eligible | Duration | The user is always ‘Eligible’ to ‘Activate’ their user role. |
| Time Bound Eligible | Duration | A user is only able to ‘Activate’ their role within specified start and end times. |
| JIT – Just-In-Time Access | This allows users to receive temporary Privileged permissions to perform tasks. This prevents unauthorised users gaining access to these after the time period has expired. | |
| Principle of Least Privilege Access | Every users is only given the minimum privileges they require to accomplish tasks they are authorised to perform. Minimising Global Administrators and instead using specific roles to accomplish tasks. |
Renew & Extend Assingments
Once you have set up a time-bound owner or member assignments, the first query you may have is’ what happens once an assignment expires? There are two options in this scenario:
• Extend – Once a user role assignment nears it’s expiration, the user is able to use Privileged Identity Management for the role assignment to be extended.
• Renew – Once a role assignment has expired, a user is then able to use Privileged Identity Management to request for a renewal for the role assignment they require.
Both of these will require approval from a Global Administrator or a Privileged Role Administrator.
Use Cases
Privileged Identity Management could be used in the following use cases;
Privileged Role Administrator permissions:
• Enable the approval of specific user roles.
• Specify users who are approvers, or groups of users to approve Privileged Role requests.
• Review Privileged Role request and approval history for all roles.
Approver permissions:
• View approvals awaiting actions.
• Approve or Reject user role requests for Priveleged Access.
• Provide reasoning for Approvals or Rejections.
Eligible role user permissions:
• Request activation of user roles that require approval.
• Review the status of your request to activate elivated user roles.
• Complete your tasks within Azure Active Directory if activation of the user role is approved.
Managed Privileged Access: Azure Active Directory Groups
Within Privileged Identity Management (PIM) you are able to assign eligibility for the membership or ownership of privileged access user groups. You are able to assign Azure Active Directory’s (Azure AD) built-in roles to cloud groups and then use Privileged Identity Management to then manage group member and owner eligibility, as well as activiation.
Important
To assign a Privileged Access Group to a user role for Admin access to Exchange, Security & Compliance Centre, SharePoint or some other select applications, use the Azure Active Directory portal Roles and Administrators options and not in the Privileged Access Groups options to ensure that the user or group is eligible for activation into the required group.
Unique Just-in-Time Policies for each Group
Some Businesses use tools such as Azure Active Directory Business-to-Business (B2B) Collaboration to invite business partners as Guests to their Azure AD Business.
Rather than just a single Just-in-Time policy for all users assigned to a Privileged Access role, you can create multiple Privileged Access groups, each of these groups can then have their own policies. You can enforce more lenient requirements for trusted employees, and much stricter requirements (such as an approval workflow) for your business partners when they require activation into their assigned user group.
Activate Multiple Role Assignments in one Request
With Privileged Access Groups, you can give workload-specific Admins speedy access to more than just a single role from a single just-in-time request.
For example, your Office Administrators may need ‘just-in-time’ access to Exchange, Office Apps, Teams, and Search Admin roles to thoroughly investigate issues. Previously, this would require four individual requests, which would take some time to process. Rather than doing it this way, you could create a user role assignable group called “Office Administrators”, assign it the Exchange, Office Apps, Teams, and Search Admin roles, and enable it for Privileged Access in the group’s ‘Activity’ option. When this has been enabled for Privileged Access, you are then able to configure the Just-in-Time settings for the users in the group and assign your admins and owners as eligible. Once the Office Administrators elevate into the user group, they’ll be granted all of the relevant Azure AD roles.
Invite Guest Users & Assign Azure Resource Roles in Privileged Identity Management (PIM)
Microsoft Azure Active Directory (Azure AD) guests area part of the Business-to-Business (B2B) Collaboration abilities within Azure AD, giving you the ability to manage external guest users and vendors, as guests in Azure AD.
You are able to use the Privileged Identity Management features for Azure identity tasks with guests. For example; assigning access to Azure resources, specifying the assignment length and end date, or requiring multi-factor authentication on the active assignment or activation.
When would you invite guest users?
For example:
• Allow external self-employed users/contractors that only have an email account to access your Azure resources for a specific project.
• Allow a businesses partner in a large organisation to use on-site Active Directory Services to access your applications.
• Allow external engineers not in your organisation (such as Microsoft or Sage support) to be able to access your Azure resources on a temporary basis to troubleshoot third party issues.
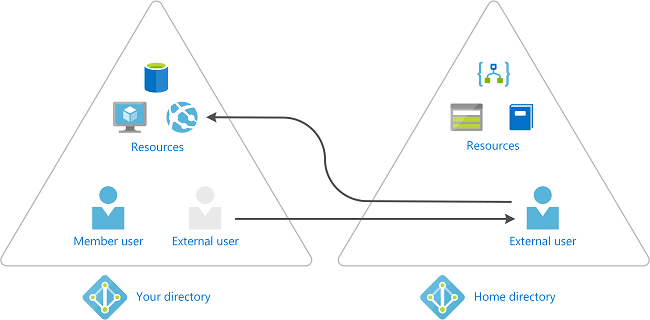
How does collaberation using Business-to-Business Guests Work?
When you use Business-to-Business Collaboration, you can invite external users into your business as a guest. These guests can then be managed as a user within your business. However, these guests have to be authenticated in their own Busienss and not in your Azure AD bsuiness. This means that if the guest looses access to their Business, they also lose access to your Business.
As an example, if the guest were to leave their current business, they will automatically lose access to resources you have shared with them in Azure AD, and you will not have to do anything to acomplish this.
Our fantastic customers include:
Contact Us
Testimonials
Aura Business Centre
Helpful, professional and fast service always!
Kevin Wood, IT Consultant
The service from Jack has been 110% throughout in line with the excellent service I’ve received since discovering One2Call. Thanks Jack and all.
Mick, MS International
Easy to get hold of and down to earth.
