Techsplained: Learn how you can spot and prevent Phishing Messages.
If you enjoyed this video we have many more on our YouTube Channel to help you improve your tech knowledge, give you advice and even “How To” videos.
Spotting phishing messages can be complex, preventing them can be easy.
Techsplained, uncomplicating technology and making it easy for you.
In this video we are talking about the different forms of fishing…. bait-fishing, fly fishing….. oh wait no!
Not that type of fishing… the other kind of phishing.
The kind where hackers and other nefarious individuals attempt to capture your data and extort you.
So, do you know what phishing is? Do you know how you can spot different forms of phishing? But most of all, do you know how you can protect yourself from phishing attacks?
This is what we are going to explore in more detail in this video and article.
What is Phishing?
Phishing is the term given to receiving a fraudulent piece of communication from someone pretending to be a person or company that they are not, in the attempt to gather information, money or otherwise extort you.
Phishing can also come in the form of an Email, Text Message, Phone Call or even Malicious Advert on a Website.
Quite often these phishing attacks will claim to be from your Bank, PayPal, Online Store or Service, Social Media, Anti-Virus, Streaming Service, a Business you deal with & even from your Government.
How can you spot different forms of phishing?
Surprisingly there are many different ways to spot phishing messages. The first is how you have received the communication.
Email Phishing
One of the most common ways of phishing is by email. And there are a few different forms of email phishing that you should be aware of and look out for.
Domain Impersonation
Domain impersonation is a method where people will send an email from an address appearing to be from a Business or Person you know.
In the below example you will see that the emails are nearly identical to each other.
See if you can guess which ones are correct or false.
[email protected]
Correct
This is the correct email address for our example.
[email protected]
Flase
This fake email address has ‘co’ at the end of the domain and is followed by the domain extension .uk .
Someone who is not looking for this may think this looks like .co.uk .
[email protected]
Flase
This false email address is again relying on people not looking too closely at the domain of the email as it is missing an ‘i’ in the address.
[email protected]
Flase
Whilst the main part of this domain may look legitimate, the domain extension is not a domain extension that “Best Banking” use and they do not advertise it on their official website or marketing materials.
The best way to tell which of these is correct is to check the domain and domain extension of the email. The Domain of an email is anything after the @ . The correct domain for the company will usually be a businesses official website domain and will be listed on official marketing materials. This can also be found easily using a search engine such as Google or Bing to find the name and web address for a business. However, remember that this may not always be the case for every business, some businesses may have more than one domain for their emails.
For example, [email protected] may also have an alias as [email protected] .
If you are ever unsure as to if the address you have received an email from is legitimate, contact the business by advertised means (Such as their Website or Google Business Listing) and you can request for a list of their “alias” addresses, some companies will also advertise these on their website.
Also be sure to check the spelling of these domains carefully as attackers rely on people not noticing subtle spelling differences or will pry on international differences in spelling.
Email Address Spoofing
As a way to get around people noticing Domain Impersonation attacks, many phishers will use a method known as email address spoofing.
Email Address Spoofing is a method by which you can make an email look as if it has come from someone without it having actually come from that person. In this case it will be much more difficult to tell if it comes in to your inbox, however the majority of email providers will see that this has not come from the official server for that domain and put this into your junk folder, this will be your first and best clue to be able to spot these types of attacks. However if your email security is not very good and these come through to your inbox you will need to use some of our other recommended ways to spot these messages.
Regardless, if these types of email are asking for you to log in, account details, payment or anything else which involves providing information or money it is always best to speak to the actual Business over the phone from a phone number advertised on their official website or Google My Business listing and not through any numbers found in the email you have received. Think of this as a verbal form of Two Factor Authentication for an email.
Name Spoofing
Name spoofing is where an email will be received from an email address other than the one for the person or company they are impersonating. However, the name displayed in your inbox will appear to be of the person or business they are impersonating, or in other cases this may show the email address of that person or business.
This avoids most junk filters as the email address it has actually been sent from is a valid one, just not for the company they are impersonating. However these are also easy to be able to spot as you can find the real email address behind the name by clicking on or hovering over it.
Lets have a look at a couplel of examples;
John Smith – Best Banking <[email protected]>
This has the name and business name of a legitimate person in the “Name” field, however the address associated with this name is a completely different email address.
[email protected] <[email protected]>
This has the email address of a legitimate person in the “Name” field, however the address associated with this name is a completely different email address.
It is important to validate the email address an email is coming from. Especially if anyone is requesting for you to log in to an account, provide details or request for payment it is always recommended to verify that the email address the email has come from is legitimate.
Attack Based Account Takeover Phishing
Another method of email phishing is Account Takeover Phishing, where an individual or company has already suffered an attack on their emails and their email accounts are already compromised. In these cases a potential attacker is sat in their accounts monitoring and using their emails without their knowledge.
The reason this is the most difficult to spot is that the email it is actually coming from the email account of the person or company effected.
They may have suffered an attack or malicious individual has gained access to one or more of their email accounts and is reading and sending emails directly from them. This is why we also need to look out for more clues. Click this link to find out how else you can spot email phishing, or keep reading.
A 2019 study found that as high as 29% of businesses had experienced an account takeover based attack over only a 30 day period.
Phone Based Phishing
Scam Calling
Phone Phishing, also known as Spam or Scam Calling, where a person will phone you claiming to be calling on behalf of an individual or company they are not.
In these cases the individuals may be attempting to capture information to access your accounts for the real company they may be impersonating. They may be attempting to capture other information such as banking information. Or they may be attempting to gain access to your computer to perform malicious activities, delete your files, record your online banking information or more.
If you want to learn more about Computer based Phone Scams such as these we recommend checking out some of videos from Scammer Payback, click here to find out more.
If you receive calls from a person claiming to be from a company that you deal with, especially if they are asking to access your account, bank details or requesting payment it is always recommended to do a reverse security check. For example, if they are claiming to be calling from your bank, ask for the last 3 digits of your account number or something else that is personal to your account. If they can not provide a verification then tell them you will hang up and call them back to the number listed on their website
If they are claiming to be calling from an anti-virus provider ask for them to confirm the account number, email address, license key or even model of computer. I (A.J.) once received a call from “BT” claiming my “Windows Computer” had a Virus, however I knew this was a Scam Call as I didn’t have any Windows computers as I primarily use Mac and Linux. Even if I did, I was not with BT for any of my services, so there would be no reason to be calling me. If I was with BT for either my phone or my internet, why would they be calling me about a virus? They are not an Anti-Virus provider.
These are all the types of things you should be thinking of when you receive calls such as this. Remember the old saying that “If it’s too good to be true, then it probably isn’t true.”, the same goes in these instances.
As a rule, no-one should ever call you regarding a virus being on your computer unless your computer’s are managed by an IT Service Provider such as ourselves. Also, Companies such as your Bank will also have strict rules about the reasons why they will contact you directly and the numbers those will come from. These will usually be listed on their website.
How can you protect yourself from Phishing Calls?
As for spam phone calls we recommend registering you phone numbers with the TPS Online, The UK’s only official “Do Not Call” register.
Once on this register it will highly restrict what companies can call you with unsolicited calls and you can report numbers through their complaint handling services.
SMS Message Phishing
Text Message Based phishing has seen a rise in recent years as it has become much more more common for Businesses to send out alerts and marketing messages via SMS. However, this has also meant a similar, if not higher, rise in SMS based phishing attacks.
One of the first things to look out for is if the message has come from a mobile number, such as: +447123 456 789
Most Businesses will send you messages from a short number such as 818283, or a message may even show their company name, such as your Bank, Mail Provider and more.
However, as this Name Generating and Number Spoofing has become more popular for SMS messages from Businesses, it has also meant that these have become more widely available for phisher’s to use also, making them much harder to spot as phishers can send message appearing to come from ‘BestBanking’ or ‘Paypal’ and so on. This is why it is important to be vigilant of the content of the messages.
What are the Clues to spotting Phishing Messages?
In this section we will show you some of the most important things you should be looking out for in the content of messages to spot phishing.
Language and Format
The very first thing that may be a give away is to look at the language and sentence structure of the message you have received. Quite often, when reading a Phishing message you will be able to tell from the language of the communication that it doesn’t look legitimate. This could be as simple as spelling mistakes, grammatical errors and even font sizes and styles changing.
If claiming to have come from an individual you email often, you may be able to tell a difference in the way their email is worded, what they are requesting or even the email structure such as a missing email footer.
However, in the case of Attack Based Phishing, where a potential attacker may have been sat in a persons account monitoring their communications for some time this can also be difficult to monitor. For example, if your colleague John has had their account compromised for the last month without their knowledge, it is possible that the potential attacker has been learning John’s language and email structure to be able to write a very convincing email as that person.
In this case it would be much more difficult to be able to tell.
Email Body Spoofing/Brand Impersonation
Another method potential phishing attackers will use is to make the emails look legitimate, they will attempt to make the emails look convincing enough to appear to have come from whom they are impersonating. This includes using things such as branding, colour schemes, logos and so on.
For example, you may receive an email that looks like it has come from Microsoft, an Anti-Virus provider or another company asking you to log in to or validate your account, reset your password or even telling you that your computer has a virus. You could even be guided to a web page that looks legitimate at first glance, however the web address will not be legitimate.
We will give you some advice of how to spot these fake links below, or you can follow this link to find out more.
In the vast majority of cases these will be an attempt to capture your log in information. For example, they may even ask for you to input your login information, and then show you a message that the information you have provided is incorrect. They may then forward you to a legitimate page for you to log in. Most people will think that the password they have entered was missing a letter, number or one of the characters was typed incorrectly which is a common error. Whereas in actual fact your login information will have been passed to potential attackers to access your account.
This is why Two Factor Authentication for all of your online accounts is important, because even if you do accidentally fall victim to one of these types of attacks you can be secure in the knowledge that even if these attackers have your email/username and password, they can not access your account without your Two Factor Authentication. You can find out more about 2FA at this link.
Request Based Phishing
Another thing to look out for is if the person or business is requesting something such as a payment or a change in their bank account details and so on, in these cases always follow these up with a phone call for confirmation to a known or publicly advertised number for these businesses and not any numbers listed in the message.
Extortion
Some scammers will use methods of extortion to scare people into handing over money, in this case cyber criminals will extort known information as leverage to attempt to get money from people. For example, these attackers could access email addresses and passwords from past data breaches on the dark web and email people directly, usually through a fake email address themselves, and try to extort money from people in exchange for not accessing people’s accounts, or even claiming to hold accounts at random in exchange for money.
Another form of this Extortion mal also be what is called ‘Sextortion’. This is a method by which attackers will claim to have intimate photos or videos gained from a users computer or webcam and is threatening sending these to a persons contacts or to websites and will only not do so in exchange for a ransom amount. In the vast majority of cases this is completely false, and in the rare instance that it is legitimate it has been known that attackers will send a sample of the content they have access to as proof of ransom.
Attachments
Another way we can spot a phishing email attempting to capture information is through fake attachments, such as PDF attachments.
One way Phishers will attempt to capture your information is to present a PDF attachment with a link saying to “view” the attachment online. This link will then guide you to a website similar to what we spoke about earlier attempting to capture your log in information for one or more services such as your bank details, Microsoft or other account details, cloud storage, social media accounts and more.
How to Spot Fake Links
When you receive a link via email, attachment or SMS message always scrutinize where it is attempting to send you.
Even though the link or the website it takes you to may look legitimate, this can just be another way to capture your information.
There are 4 main parts of a link to consider to check for it’s legitimacy, lets take a look at this example fake link: http://paypal.mycompany.co/login
http://
The Security & Encryption
This is at the beginning of the address. A secure address with encryption will begin with https://
Almost all websites that ask you to log in with details will have SSL, or HTTPS, security. Especially major companies such as Banks, PayPal, Social Media, Anti-Virus and so on.
paypal.
The Sub Domain
This is the bit before the domain, in this example it is PayPal
The most important thing that you should remember when looking at a web address like this is that any website can have any sub domain of it’s choosing and it requires no authentication or varification with any governing body.
mycompany.co
The Domain
This is the primary part of the address that most people will need to look out for. One thing that you should look out for in a domain is the domain extension.
This is often .com , .co.uk , .net , .biz and so on. However attackers will purchase domains with extensions such as .xyz or .co as to an untrained eye these may look legitimate.
/login
The Slug
This is anything after the forward slash after the domain. In this example it is /login
Similar to Sub Domain’s though, it is important to remember that any website can have any slug of it’s choosing. We could give any page on our website any slug we want. Slugs can also include multiple dections divided by more /’s.
If we wanted to, we can make paypal.one2call.net/paypal and direct it to any page of our choosing, or we could build a page to look like a PayPal log in page. Just because the sub domain or slug contains the name or something to do with a company does not make it legitimate.
The most important part of this address is the domain and domain extension, this is where we want to see the legitimate web address. For example if PayPal are emailing you it will list PayPal.com, and not palpal.co or .xyz and so on.
Similar to the Subdomain and Slug, these Domain Extensions such as .xyz or .co may not always be legitimate. Many potential attackers will purchase web domains such as .co or .uk or even .bank so that they can use these addresses for potential attacks.
Most people do not know this, but you can often check the domain owner by going to a website such as whois.com/whois and you can type in the domain to see who the owner is. Many major corporations will not hide this information so that you can prove that they are the owners of the domain. Such as your Banks, Social Media Companies, Online Stores and so on.
Phishing Message Examples
Example 1
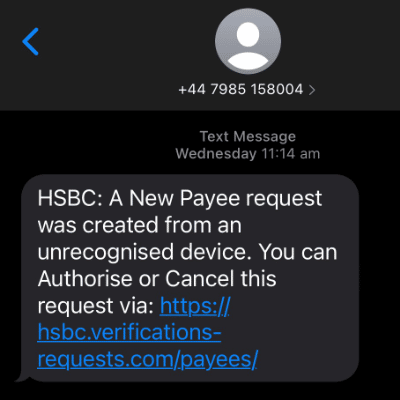
In this exmaple of SMS phishing you can see that the sending number is a regular mobile number rather than. ashort code or business name. Whilst the message content may look legitimate, the URL/Web Address is a fake link. The Business name “HSBC” is the SubDomain (Which anyone can make), the domiain is nothing to do with the business & the slug is referring to the message content.
Example 2
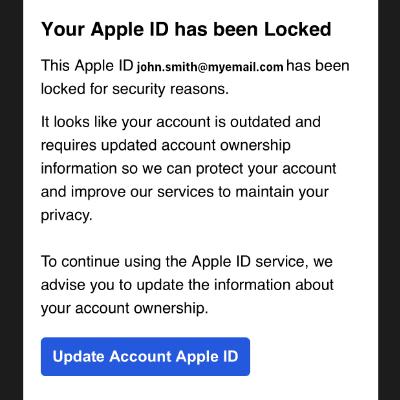
In this example of Brand Impersonation phishing you can see that the email looks legitimate, the wording is correct, the formatting is correct, however the button guides you to a fake website. and the email address it has come from is. acompletely fake email address that has nothing linked to the supposed sender (See Example 4 for more.)
Example 3
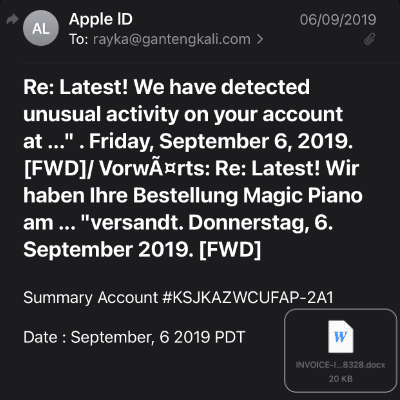
This example of Band Impersonation uses Attachment Based Phishing, the “Name” name of the sender looks legitimate (See Example 4 for more.), the subject is worded in a way to attempt to scare a potential victim, and the attachment on the email includes a link to a fake website much like in Example 1 & 2.
Example 4
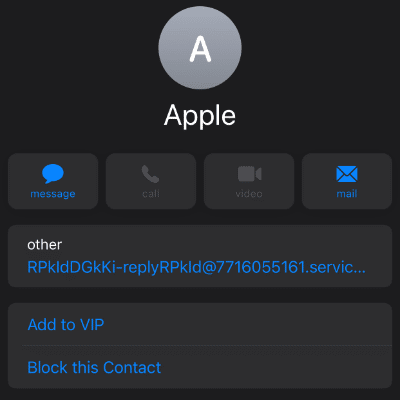
In this example of Name Spoofing you can see that the “Name” of the account which you have been sent an email from looks correct much like in Example 2 & 3. However, when investigating the email address behind the account “Name” you can see that the email address is complete jibberish, this is done in an attempt to confise a potential victim.
What do attackers do with this information?
Once potential attackers have access to your accounts they could potentially alter your passwords to restrict your access, purchase things in your name & monitor your emails, which could potentially lead to them Impersonating you.
In a business this could lead for them to request your customers or clients change bank details or request payments to different bank accounts and more or they could start to send emails out to start a new attack from your email address and potentially even to further access and infect your systems or other accounts if you reuse your passwords elsewhere (which you should never do).
How can you protect yourself?
The first thing you can do is to keep an eye out for many of the things that we have discussed in this video and article.
Secondly, we recommend you check out our videos on best practices for passwords and also you activate Two Factor Authentication or One Time Password on as many of your accounts which support it.
However, if you want to go a step further towards protecting yourself you can look at professional grade Active Email Threat Prevention. One2Call’s Active Email Threat Prevention service can monitor your email accounts using Artificial Intelligence Based Real Time Monitoring to check for the legitimacy of emails you are receiving and even quarantine spam or potentially risky emails. It can identify high risk members of your business that it can highlight as potential targets of cyber attacks, it can prevent against account take over and with our fully managed service we can be alerted of any potential attacks or threats against any of your users.
We can also offer your business active Dark Web Monitoring services to monitor either a single email addresses or entire domains. So that you can see if any of your personal or business passwords have been leaked on the dark web so that you can change passwords on accounts which use the same login details.
If you feel that either or both of these services would be useful for you or your business fill out the form below to get a FREE Dark Web Scan & FREE Mailbox Security Scan.
We’ll also be producing more content on this and other tech topics in future, so be sure to subscribe to our socials and subscribe to Techsplained and TechBytes to be the first to know about future content.
We hope you have found this information useful. Leave us a comment over on our YouTube Channel to let us know what you think or to ask a question.
FREE Cyber Security Scans
Testimonials
Aura Business Centre
Helpful, professional and fast service always!
Mark, Modern Creatives
Speed of response and excellent customer service, we like working with smaller local suppliers rather than faceless national providers for these reasons.
Claire H, MSP PLC
Made a call into day, to arrange an engineer visit and was able to get there before 12noon and solve the issue.

